Find Transposition Errors Before They Turn into a Bigger Issue
In business, however, entering the wrong sequence of digits can lead to serious, even disastrous consequences. If you have information coming in that’s off, being miscategorized, or just all-around wonky, there’s a good chance there’s been a misuse of accounting software. Among Windows 11 error codes, “0x0 0x0” is among the most ubiquitous and most difficult to pin down the direct cause of.
A new patient-specific overformed anatomical implant design … – Nature.com
A new patient-specific overformed anatomical implant design ….
Posted: Fri, 24 Feb 2023 08:00:00 GMT [source]
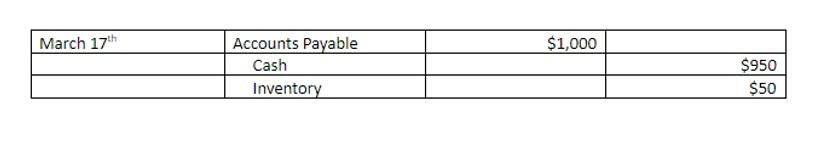
Then ask, “Is it part of accrued revenue, accrued expense, deferred (unearned) revenue, or deferred (prepaid) expense? ” Once those steps have been discovered, an adjusted journal entry is created to fix it. A particular example of an error of original entry is a transposition error where the numbers transposition error are not entered in the correct order. For example, if cash paid to a supplier of 2,140 was posted as 2,410 then the correcting entry of 270 would be. For example, suppose the trial balance showed total debits of 84,600 but total credits of 83,400 leaving a difference of 1,200 as shown below.
Transposition Error, the Little Mistake That Causes Big Problems
You can also take some of the pressure off with services like QuickBooks Live — receive professional help to catch these errors for you so you can focus on your other small business needs. An example of a principle error might be buying a piece of equipment and miscategorizing the expense as a sale instead of a purchase. Such a snafu could wreak havoc on your checks and balances when it comes time to reconcile your financial statements. This can have an impact on the income statement and indicate inconsistent and inaccurate financial incorrect records. The following example shows how to tell if there is a transposition error. For purposes of illustration, a partial trial balance is shown using account balances without the account titles.
- It goes without saying that over or under-compensation doesn’t look good on the books, but it’s also not good for rapport within your organization.
- In 1992, 96 people onboard Air Inter Flight 148 died when it crashed into a mountain due to a transposition error.
- Duplications are another common accounting error that is the result of double-entering an income or expense entry.
- Your Guide to Starting a Business The tools and resources you need to get your new business idea off the ground.
- If it is not, then the error is a slide, which can only be corrected if the amount is evenly divisible by 3.
To spot the errors, find the difference between the recorded amount and the correct amount. See if correcting the error will increase (I) or decrease (D) the debit or credit total. Chartered accountant Michael Brown is the founder and CEO of Double Entry Bookkeeping.
What is the difference between a transposition error and a slide?
Find the difference between total debits and credits, add 1 to the first digit of the difference, and you have an amount we will call X. You will now investigate every ledger account balance in which the difference between the first and second digits of the balance is X. Transposition errors must be corrected, since they https://www.bookstime.com/ will otherwise result in incorrect numbers in the financial statements that may be material. Here’s an example from Mastering Correction of Accounting Errors, Section 3 – Finding and correcting errors using the unadjusted trial balance. To determine if it’s a transposition error, find the difference ($1,810 – $1,180).
- Reviewing your trial balance (via your accounting software) is one way to find different types of errors.
- The most obvious example is text entry speed, measured, for example, in words per minute.
- The easiest way to prevent any changes after close and avoid closing errors is to set a closing password.
- A lot can go wrong in Windows that can lead to it popping up, so troubleshooting involves the trial and error of attempting different fixes until one works.
- Our goal is to deliver the most understandable and comprehensive explanations of financial topics using simple writing complemented by helpful graphics and animation videos.
- You cannot tell which of the two marked values is responsible for the error; in fact, you cannot be certain that it was a transposition that caused the error.
Take a look at the examples below to learn how a simple transposition error can affect your small business. Now that you know what is transposition in accounting, you might wonder where these errors can occur. Transposition accounting might creep into your journal entries, business ledger, financial statements, or invoices. You can also inadvertently flip-flop the numbers of an employee’s wages while writing their paycheck. Millions of federal student loan borrowers all resumed repayment last month for the first time in over three years, following the end of the student loan pause.
Ask a Financial Professional Any Question
OK, so now let’s get back into the transposition mistake magic “9” identifier. All transposition error discrepancies are divisible by the number 9. If your discrepancy is evenly divisible by the number 9, you may have a transposition error on your hands. Not only does this mistake result in lower wages for your employee, but it also leads to costly tax miscalculations.
- Published in Bookkeeping
What is a proxy server and what is it used for?
A proxy doesn’t encrypt your data and doesn’t offer complete anonymity or security. If you want to use a proxy server to stay anonymous while surfing the web, you’ll have to take into account a lot of different factors. In most cases, it’s much safer and much more practical to use a VPN server instead of a proxy. They act as buffers because they can connect to the internet and send requests from computers outside the network.
Hardware-based proxy servers are deployed on dedicated hardware, offering a larger scale to handle massive traffic. In addition, they are equipped with additional storage https://deveducation.com/ to enable content caching and monitoring. A web proxy listens to web traffic contained in TCP/IP packets and acts at the client’s behest to request the web server.
WHAT THEY ARE SAYING: President Biden Issues Executive Order on Safe, Secure, and Trustworthy Artificial Intelligence
Because they are shared by others, you may get blamed for someone else’s bad decisions, which could get you banned from a site. A high anonymity proxy is an anonymous proxy that takes anonymity one step further. It works by erasing your information before the proxy attempts to connect to the target site.
You may like the idea of using an anonymous proxy to protect your privacy, but keep in mind that on its own, a proxy server affords limited security because its data isn’t necessarily encrypted. Without encryption, it’s not difficult for a motivated third party to learn a lot about the browsing activities of anyone using the proxy. A proxy server can allow originating computers to masquerade as different computers – and more importantly, appear to be located in completely different geographic locales. When computers connect to the internet, they use an IP address that marks outgoing data with a return address. Likewise, a proxy—either a private or open proxy—acts as another computer on the internet with its own IP address.
Transparent vs. Non-Transparent
A proxy server can protect against malware and cyber attackers and is especially useful when merging with a Virtual Private Network (VPN), commonly used by companies for security purposes. HTTP proxies can be used to bypass internet filtering proxy internet definition and website restrictions. This enables users to avoid security controls and filters that block access to prohibited websites. An HTTP proxy acts as a high-performance content filter on traffic received by an HTTP client and HTTP server.
Essentially, it’s like a middleman, passing information from your device to the internet and vice versa. Overall, it can be said that the proxy server accesses the targeted site, on behalf of the client, and collects all the requested information, and forwards them to the user (client). The following figure clearly depicts the working of the proxy server. The use of proxy servers is increasing rapidly for enhanced security and privacy. Future developments may include advanced protocols, AI and machine learning integration, cloud proxies, improved security features, and enhanced scalability.
- Published in IT Education
What is Social Trading, its Benefits and Top Social Trading Platforms by Katalyse io Coinmonks
The verified real-time updates help the investor in ascertaining the reasons for the spike in the trading market. It helps the average trader follow the Big Investors like Warren Buffett, as they trade on the stock market, helping the investor in making informed decisions rather than relying on instinct. Competitive trading will always have its place, and some people live for it, but it’s good to have an alternative, and social trading is the perfect answer for people looking for a radically different approach. It isn’t about simply taking a quick look at who is doing well and then copying every move they make. Online trading platforms that promote social trading provide you with a number of tools to make full use of the sophisticated investing principle.
Consequently any person acting on it does so entirely at their own risk. Any research provided does not have regard to the specific investment objectives, financial situation and needs of any specific person who may receive it. It has not been prepared in accordance with legal requirements designed to promote the independence of investment research and as such is considered to be a marketing communication. Although we are not specifically constrained from dealing ahead of our recommendations we do not seek to take advantage of them before they are provided to our clients. Social trading platforms enable you to search for, and locate, traders whose styles match your online trading needs. Each trader’s decisions are based on their individual trading plan, their goals, motivation, risk tolerance and capital available.
- At the heart of this choice is the goal of solving a customer’s problem.
- This is done through social trading platforms, which make it easy and convenient for investors to check out other traders’ activity, then implement those same moves in their portfolio.
- For example, Elon Musk causes an earthquake on the financial market with his every tweet.
- The core principle of social trading is the ability to follow the investments of other traders in the community.
- Social trading is profitable, but you should evaluate your risks correctly and never invest money you cannot afford to lose.
This is thanks to the availability of many top social trading brokers and platforms like AvaTrade and others, combined with an increasing desire for social interaction online. Here we will examine exactly what social trading is, how to get started in social trading, and some of the ways in which it could benefit your forex trading future. Social investing is gaining in popularity as more investors rely on each other to guide investment decisions.
Also if you graduate from the program as a top student or you get voted as the top instructor in the CST program, you will be rewarded in Tokens. The tokens will essentially allow users to access the Spiking Platform and its services. Social trading is profitable, but you should evaluate your risks correctly and never invest money you cannot afford to lose.

Thanks to modern technologies, it has never been easier to become a “social trader”. You can implement the entire setup or specific components using a complete social trading platform. It’s related to but not the same as copy trading, in which one investor copies the trades or investments of another.
This means you can follow other traders, post comments, messages, and share your opinions through the network. It’s important to always understand why you are making https://www.xcritical.in/ a certain decision and have an appropriate risk management strategy in place. We’re going to look at each of these in turn, and alternative ways to trade socially.
From there, you can create your account and start searching for investors to follow. Implementing a social trading strategy may be as simple as clicking a button to mirror another investor’s entire portfolio. As impressive as social trading may sound, it is not without its limitations. While it does present several alluring advantages to both novice and experienced traders, there are still some limitations you should be aware of.
Thinking of social trading as copy trading combined with social media will get you close to an accurate picture of what social trading is. Working with an adviser may come with potential downsides such as payment of fees (which will reduce returns). There are no guarantees that working with an adviser will yield positive returns.
Your trading plan should always be unique to your situation and it’s important to understand why a trader you follow is making a certain trade. It’s also important to keep in mind that you should never blindly trust a third party’s judgement, without any prior knowledge or market research. Traders might be wrong and some might even share wrong information on purpose. All trading involves risk, and all traders are likely to make a loss at some point in their journey. Today, we will dive so so deep into this topic, that by the time you finish reading, you would want to abandon the social media platforms and start social trading. One of the most common ways to identify trends and the inclinations of other traders is to use market sentiment.
A recent survey of Gen Z aged between 13 to 26 by Morning Consult found that a staggering 57 per cent of them would be happy to trade their day jobs for a career in influencing. On Monday, the Internal Market and International Trade committees adopted their position on keeping products made using forced labour out of the EU market. With this in mind, analyze how this product will get to your customers.
The often more experienced traders who choose to share their trades can generate additional income by becoming influencers. Most social trading platforms pay traders a bonus based on the number of traders who are following and copying their trades. Similar to social networks, the social trading platform offers a similar rating to experienced traders, where they share their trading tactics and other information.
Discover why so many clients choose us, and what makes us a world-leading provider of spread betting and CFDs. Since all the bets placed are tracked in real-time, Trinkerr ensures that there is complete transparency in the information that the users have access to. If you have ever bet on social trade work sports, you likely found sites which give tips on what you should bet. IG International Limited is part of the IG Group and its ultimate parent company is IG Group Holdings Plc. IG International Limited receives services from other members of the IG Group including IG Markets Limited.
To understand how “shared” trading is utilized by market participants, we must first mention the most commonly used methods developed to do so. These are various trading methods that differ in a range of key aspects. The good thing is that almost every proper Forex broker nowadays offers such a solution. Currently, the service is a BETA version and it can be completely free both for traders and copy traders.
- Published in FinTech
CompTIA Security+ Certification Boot Camp
You can then download our free training plan worksheet to customize your training and get organized. TCCIT Solutions provides high quality, affordably priced, training classes in CompTIA Network+. With experienced instructors and a convenient midtown NYC location, we offer CompTIA Network+ courses for the corporate community. TCCIT Solutions offers group classes and CompTIA Security+ Lessons private tutoring to beginner and more advanced corporate clients in CompTIA Network+. We offer onsite training or classes at our facility on 34th Street and Madison in New York City. Global certification that validates the hands-on skills of IT professionals who install, manage and troubleshoot servers in data centers as well as on-premise and hybrid environments.
- Their practical knowledge of IT systems ensures they understand how to maintain, troubleshoot and optimize network and system performance.
- Get started with comptia security for free and learn fast from the scratch as a beginner.
- Second, technology solutions do not work in a vacuum but are dependent on each other to operate effectively.
- This course pack provides a range of curated IT courses, including CompTIA IT fundamentals, networks, servers, Linux, CySA, and more.
- Network experience is helpful but not required; A+ certification or the equivalent skills and knowledge is helpful but not required.
Select free courses for comptia security based on your skill level either beginner or expert. These are the free comptia security tutorials and courses to learn comptia security step by step. CompTIA training products use a multi-faceted approach, are designed to follow exam objectives and offer a variety of options to meet the needs of different types of learners at different stages of their training.
CompTIA Security+ (Exam SY0-
If you consistently struggle with specific topics, you can allocate more study time to those areas. For example, one of the most challenging aspects is the networking portion, which includes IP addresses, binary and decimal number conversion, and hexadecimal. Preparation involves practicing these concepts, especially converting binary to decimal and vice versa. If this is an area you find yourself struggling to master, you may need to refine your preparation plan and spend more time studying networking.
The course was extremely helpful and provided exactly what we needed to know in order to successfully navigate the exam. The Security+ fulfills the requirements for Department of Defense (DoD) Directive 8570, which is mandatory if you are looking to get a government job that is involved with any aspect of information security. Second, on all CompTIA exams, there is a timer; however, with PBQs, this timer is not visible to the test taker.
6 – Embedded Systems
Earning CompTIA Security+ helped cybersecurity specialist Vina squash imposter syndrome, deepen her knowledge of IT security and reinforce her passion for working with people. Includes applying and enhancing security and vulnerability management techniques, as well as security implications of proper hardware, software, and data management. Each CompTIA product category corresponds to a learner’s progression in attaining tech skills and competencies. CompTIA certifications are powerful and respected credentials that employers trust and will give you the opportunity to thrive in your career and achieve your income goals.

With a successful training approach, you can test with confidence, pass your exam and get certified. Plus, these skills will serve you well on any CompTIA exam you decide to pursue. Now that you’ve reviewed the exam objectives and have an idea of what you need to prioritize, it’s time to study.
Certification
So no matter what method you choose, you know that what you’re studying is what you’ll see on the test – and what you need to know to help keep organizations secure. CompTIA Security+ is the most widely adopted ISO/ANSI-accredited early career cybersecurity certification on the market with hands-on, performance-based questions on the certification exam. Additionally, CompTIA Security+ maps to National Institute of Standards and Technology (NIST) work roles, as well as their respective DoD DCWF work roles. It comes as no surprise that cybersecurity continues to be one of the most sought-after IT job roles in the tech industry. Perhaps you’re currently working as a help desk technician and you’ve gotten a glimpse into a few cybersecurity projects that have sparked your interest, and you’re ready to take that next step. Regardless of whether you’re already in a cybersecurity-specific role or you’re doing cybersecurity tasks in a more general IT role, tech pros need cybersecurity skills to succeed.
I really appreciate that our instructor was extremely knowledgeable and was able to provide the information in a way that it could be understood. He also provided valuable test-taking strategies that I know not only helped me with this exam, but will help in all exams I take in the future. The internationally recognized CompTIA Security+ certification is a sought-after and high-demand credential for information security professionals seeking to enter the cybersecurity job market. The average salary of a CompTIA Security+ certified professional is $78,000 in the U.S.
What Comptia Security+ courses are best for training and upskilling employees or the workforce?
Preparing for the exam process under simulated testing conditions will get you the rest of the way there. CompTIA CertMaster Practice is an adaptive training tool that assesses your knowledge and exam readiness by finding knowledge gaps and helping you fill them quickly. Virtual labs are interactive, online environments or platforms that allow individuals to learn and practice skills in a simulated setting. What sets CompTIA CertMaster Labs apart is that you’re working on real equipment and software – not just in a simulation. You can use CertMaster Labs in two ways – with instruction, so you can learn new skills, or on your own, practicing what you already know.
- Aligned with Official CompTIA courseware and the CompTIA A+ exam objectives.
- The CompTIA career roadmap can help you see how your cybersecurity career could progress as you gain skills and experience.
- The A+ certification is also essential for setting IT pros up on a career path in the field.
- The resources, support, and certifications it offers IT professionals and organizations are widely respected throughout the industry and world.
Upon completion, delegates will have the practical expertise to proactively identify and mitigate security threats, making them crucial assets in maintaining the integrity of IT systems and data. They will also be well-prepared to address the evolving challenges in the cybersecurity landscape. With this certification, you can support your organization in various roles to identify potential security threats, improve incident response and more.
- Published in Education
Full stack: o que é, quanto ganha e como é ser um desenvolvedor
Porém, em muitas empresas esses papéis se fundem e por isso é bem comum que devs back-end assumam as atribuições de DBAs. Este Pacote é inédito e único, pegamos os melhores cursos da nossa plataforma e reunimos em um único pacote para você levar tudo de uma vez só. Siga este guia abrangente para descobrir exatamente o que é um desenvolvedor full stack e como se tornar um. Assim, esse perfil de profissional é altamente valorizado no mercado de trabalho, pois ele possui a flexibilidade para atuar em qualquer área do projeto e dessa forma ajudar no crescimento e desenvolvimento dos mesmos. Compreende-se então, a partir do que foi apresentado, que um Desenvolvedor Full Stack precisa ter conhecimento de tudo que envolve uma aplicação.
Aprenda em um curso completo como criar qualquer layout e interface para Web! Siga esses 8 passos, ganhe uma vantagem competitiva e aprenda a como programar como um profissional. A Accurate está sempre incorporando em seus projetos o melhor da tecnologia e dos profissionais do mercado de TI. A busca por desenvolvedores Como se tornar um analista de dados? cresceu muito nesse período para que essa transformação digital aconteça o mais rápido possível e se adeque a essa nova realidade. Você também pode tentar se inspirar no que os outros estão fazendo em seu espaço.
Mais de 200 projetos práticos
Além disso, por seu conhecimento em várias áreas, esta pessoa tem uma visão geral das necessidades dos usuários, o que pode ser um diferencial em projetos em que a experiência do usuário é fundamental. Full stacks podem trabalhar em conjunto com especialistas, garantindo que haja uma integração fluida entre as diferentes áreas do projeto. Essa é uma das stacks mais populares, principalmente no desenvolvimento de aplicações web escaláveis. Ela é formada pelo MongoDB, para a parte de banco de dados; O framework de desenvolvimento web Express para o back-end; e o Angular para o front-end. Indo mais além, você pode criar serviços para fazer interface com o seu back-end. Você pode automatizar a criação desse banco de dados usando CloudFormation ou scripts bash.
- Conhecimentos gerais sobre como funciona a internet e seus principais mecanismos podem inseri-lo com mais confiança no setor, enquanto quanto mais linguagens ele conhece, mais competitivo é seu perfil.
- Cedo ou tarde, você usará essas funções para se conectar a outros serviços e bancos de dados para criar seus próprios serviços dinâmicos.
- Ainda que seja um profissional multitarefa, um full stack não costuma trabalhar sozinho.
As bibliotecas, por exemplo, são grandes fontes de códigos, verdadeiras coleções que podem ser acessadas. Isso porque eles ajudam a resolver problemas específicos de maneira muito mais prática e ágil. Muitos livros e mesmo comandos de códigos e linguagem são em outros idiomas. Nem só de competências comportamentais se faz um profissional, ainda que elas possam ser grandes diferenciais no mercado de trabalho.
O que não é full stack
Ele é responsável pela apresentação visual do sistema, ou seja, pelo que o usuário vê e interage. Curso focado em ensinar programadores a usar todo poder do marketing digital para alavancar suas vendas e conseguirem vender qualquer projeto. As mesmas técnicas de aprendizagem e produtividade, que utilizamos na Danki Code, em um curso completo para você! Este é um curso excelente para quem quer ter uma vida saudável e sempre estar com energia. Este site usa o Google Analytics para coletar informações anônimas, como o número de visitantes do site e as páginas mais populares. Ele é então, um profissional que contribui em qualquer lugar dentro de uma equipe de desenvolvimento conforme a necessidade do projeto.
Investor Relations – CISCO REPORTS FIRST QUARTER … – Cisco Investor Relations
Investor Relations – CISCO REPORTS FIRST QUARTER ….
Posted: Wed, 15 Nov 2023 21:06:58 GMT [source]
Este desvio é devido a vários fatores, incluindo educação, experiência, responsabilidades no trabalho, a empresa (e sua rentabilidade), a localização do trabalho e se a posição inclui benefícios. https://www.acessa.com/tecnologia/2023/11/186143-dicas-para-escolher-o-melhor-curso-de-cientista-de-dados.html Mas o que é um desenvolvedor full-stack, o que eles fazem, e como você se torna um? Continue lendo, e nós lhe diremos tudo o que você precisa saber sobre como ser um desenvolvedor full-stack.
- Published in Bootcamp de programação
Qué necesitas para ser Científico de Datos o Data Scientist
Esta web utiliza Google Analytics para recopilar información anónima tal como el número de visitantes del sitio, o las páginas más populares. Con una sintaxis clara y fácil, muchos recién iniciados optan por este https://voxpopulinoticias.com.mx/2023/12/un-bootcamp-de-programacion-que-te-prepara-para-tu-nueva-profesion/ lenguaje, así como aquellos que vienen de ingenierías informáticas. Otra de las claves es que es un lenguaje que no tiene únicamente un enfoque estadístico, sino que puede ser utilizado para otros propósitos.
- Si tuviéramos que definir la ciencia de datos en una forma resumida, podríamos decir que la ciencia de datos (o Data Science) es la disciplina que convierte los datos en conocimiento útil.
- Ahora, esto es probablemente un punto más relacionado con la ¨motivación¨, pero ten en cuenta que tendrás que mostrar buenos resultados desde el comienzo de tus estudios para poder seguir una trayectoria profesional como data scientist.
- Hay dos ramas muy populares en la ciencia de datos que una persona buscando cómo convertirse en data scientist debería conocer – el análisis de datos y la ingeniería de datos.
- Los científicos de datos suelen tener un título de postgrado en una materia técnica como la informática o la estadística.
- Habilidades difíciles de reunir, gran impacto en el negocio y el hecho de que viene precedido de un boom.
Esto implica aplicar técnicas estadísticas y matemáticas para comprender y extraer información relevante de los conjuntos de datos. El científico de datos utiliza herramientas y algoritmos de análisis de datos para identificar patrones, tendencias y relaciones, lo que permite tomar decisiones basadas en evidencia. Por lo general, las responsabilidades de un científico de datos pueden coincidir con las de un analista de datos, en particular en el análisis de datos exploratorio y la visualización de datos. Sin embargo, las habilidades de un científico de datos suelen ser más numerosas que las de un analista de datos típico.
Mejores Cursos de Ciencia de Datos: Cómo ser científico de datos
Por ejemplo, para saber cuál es el mejor momento para comprar un billete de avión, predecir los gustos de los usuarios y mostrarle la mejor opción o descubrir si una persona puede tener riesgo de padecer una enfermedad. Autor de cursos de formación en tecnologías Big Data, Cloud y Streaming completados por más de 5000 alumnos en Udemy y otras plataformas. Es importante tener en cuenta que estas son solo cifras aproximadas y que el salario real puede variar ampliamente según la ubicación, la industria y el nivel de experiencia.
Si estás considerando convertirte en un científico de datos y seguir los próximos pasos, primero debes centrarte en tu educación. Para muchos científicos de datos, la inversión curso de ciencia de datos en su educación es una de las mejores inversiones que hacen. Puedes inscribirte en un colegio, una universidad o un bootcamp para ampliar tu formación como científico de datos.
Empieza a construir tu carrera en ciencia de datos y analítica
Como vimos, los científicos de datos se desarrollan dentro de un campo de estudios interdisciplinario que pone en juego herramientas, instrumentos y técnicas de diversas áreas de estudio. Hoy en día, todas las empresas se sirven de los datos para tomar decisiones y crear mejores productos y servicios. El uso de tecnologías de código abierto está muy generalizado en los conjuntos de herramientas de ciencia de datos.
- A partir de estas preguntas, el profesional crea modelos estadísticos y matemáticos para tratar de determinar quiénes son los clientes que harán clic en el correo electrónico y cuáles no.
- Hay muchas personas que quieren saber cómo convertirse en un data scientist porque desean su sueldo.
- Un Data Analyst o analista de datos se centra principalmente en la recopilación, el análisis y la visualización de datos.
- «Alguien viene a mí con un problema», explicó, «y puedo traducirlo en algo que se puede resolver con matemáticas y construir un modelo a su alrededor».
- Para realizar estas tareas se requieren fundamentos en matemáticas, estadística y métodos de optimización, conocimientos en lenguajes de programación y que además tiene una experiencia práctica en el análisis de datos reales y la elaboración de modelos predictivos.
Si te interesa saber cómo ser científico de datos, después de analizar los datos recopilados durante los estudios, el curso demuestra con precisión cómo es un día en la vida de un científico de datos. MIOTI Tech & Business School es considerada una de las instituciones más respetadas en España. Como escuela recomendada, sus cursos acreditarán y robustecerán tu hoja de vida, para que puedas entrar a cooperar con empresas grandes. El perfil de un científico de datos le permite obtener salarios bastante altos en su campo de acción. Jennifer Hobbs, científica senior de datos para STATS, una compañía de datos deportivos, explicó que algunas compañías usan el título de trabajo de científico de datos como un todo.
Construyendo una carrera en ciencia de los datos: Una guía de cómo hacerlo
Los nuevos instrumentos permitían realizar una nueva gama de experimentos y resultaron en el nacimiento de nuevas especialidades como la meteorología, la anatomía microscópica, la embriología o la óptica. También es importante mencionar que por el momento Udacity no ofrece cursos gratuitos de ciencia de datos. EdX ofrece la oportunidad de inscribirse en los módulos como cursos individuales de ciencia de datos, lo que hace que cada uno tenga un precio por separado de aproximadamente $149. Además de eso, tienes la opción de auditar gratis los módulos de los cursos, aunque esto limita las funciones disponibles, como el que no podrás obtener una certificación al finalizar. Todos los módulos del curso incluyen múltiples videos educativos y ejercicios de práctica, que cubren el qué, el por qué y el cómo de la ciencia de datos.
- Published in Bootcamp de programación
A Revolução da Informação: curso gratuito traz palestras sobre IA e Big Data
Se você ainda não sabe trabalhar com um dos principais provedores de Cloud Computing (AWS, Microsoft Azure e Google Cloud) comece imediatamente. À medida que mais e mais organizações estão se tornando centradas em dados, os princípios do Agile para desenvolvimento de aplicativos e monitoramento da integridade operacional dos aplicativos também serão relevantes para os dados. Apesar disso o que torna as AI’s tão impressionantes ainda é a criatividade humana e a sua capacidade de delegar funções a esses sistemas. Apesar de existir já a um tempo, a AI (Inteligência Artificial) tem se tornado popular no mercado comercial recentemente. Outra funcionalidade de automação de dados que tem crescido muito e que vai impactar o mercado nos próximos anos são os softwares de CRM (Customer Relationship Management).
Além disso, a criação de modelos preditivos pode ser usada para prever eventos futuros com base em dados existentes, o que pode ser útil em áreas como previsão de desastres naturais e planejamento urbano. Ainda podemos observar que a combinação dessas tecnologias também pode ser usada para melhorar a gestão ambiental e o agronegócio, permitindo uma análise mais precisa e eficiente de dados espaciais relacionados a essas áreas. A Inteligência Artificial é uma tecnologia que permite que as máquinas aprendam e tomem decisões com base em dados.
Acesse, em primeira mão, nossos principais posts diretamente em seu email
No entanto, preocupações com a segurança dos dados e a complexidade operacional significam que essa exploração será medida e estratégica. A AI generativa, conhecida por sua habilidade de criar conteúdo e fornecer respostas inteligentes, está capturando a imaginação do mundo tecnológico. Pós-graduada no curso de especialização em Big Data e Comunicação, bacharela em Comunicação Social – Jornalismo e Tecnóloga em Design Gráfico.
- Os profissionais de BI que se adaptarem a essas tendências estarão bem posicionados para ter sucesso no futuro.
- É uma tecnologia importante que pode ajudar as empresas a tomar decisões mais rápidas e informadas.
- A análise de dados, principalmente no campo do Business Intelligence (BI), está cercada por preocupações crescentes relacionadas à privacidade e ética.
- A Inteligência Ativa é uma proposta que se aplica perfeitamente à realidade do mercado atual, e não há dúvidas de que os dados capazes de acionarem ações imediatas serão objetos de grande valor analítico no futuro.
- As organizações terão a responsabilidade de utilizar os dados de forma transparente, evitar vieses e proteger a privacidade dos indivíduos.
- As estratégias de análise de dados (D&A) sejam vistas com mais frequência como ativadores essenciais para lidar com os atuais desafios dos negócios, bem como um meio para abordar oportunidades futuras.
Isso destaca como a pesquisa de mercado, a colaboração, a prototipagem e a iteração são elementos-chave no processo de inovação e desenvolvimento de produtos. Ao alinhar os produtos com as necessidades do mercado e oferecer recursos inovadores, a empresa pode impulsionar o sucesso e a competitividade no setor. À medida que a IA se tornar mais acessível, é provável que seja cada vez mais adotada pelas empresas para análise de dados. Dessa forma, preparar as equipes e os profissionais para lidar com essas novidades faz toda a diferença. O uso de banco de dados estáveis, com criptografia avançada para garantir a confidencialidade e o acesso devido a essas informações, só pode ser realizado com um vasto conhecimento na área. Para isso, é necessário contar com um banco de dados, pronto ou criado a partir da maneira que o programa é alimentado, para comparar informações e identificar semelhanças entre os elementos.
Análise de Dados em 2023: Desvendando o Futuro da Tomada de Decisões Estratégicas
Os profissionais de BI que estão preparados para a IA estarão bem posicionados para prosperar no futuro. A ciência de dados é uma das principais responsáveis pela aplicação dessa tecnologia e permite estruturar um algoritmo mais preciso e eficiente. Em outras palavras, a transformação digital é o principal fator que movimenta o ramo da ciência dos dados. Uma vez que esse campo se desenvolve, a necessidade de coletar, https://surgiu.com.br/2024/02/17/curso-de-analista-de-dados-como-bootcamp-da-tripleten-prepara-voce-para-o-mercado/ tratar e analisar informações de forma otimizada e estratégica aumenta. Esse é apenas um exemplo de como o campo da ciência de dados faz parte da realidade dos mais variados setores com perspectivas positivas de crescimento. Mais uma vez destacamos que a combinação de Geoprocessamento e Inteligência Artificial está revolucionando a análise de dados espaciais e abrindo novas possibilidades para o futuro.
O Promoview é um canal de conteúdo especializado em Brand Experience que pauta o mercado desde 2006. Sempre acreditamos na experiência como a plataforma mais genuína e estratégica de conexão entre marcas e pessoas, e existimos para potencializar todo o segmento que pensa, produz e entrega trabalhos incríveis em todo o país. Quando revisitamos a história da humanidade, desde o Paleolítico, o uso de tecnologia curso de analista de dados ajudou a alavancar a espécie e gerar desenvolvimento. Foi assim com o fogo, com a roda, a energia elétrica, exemplos não faltam para ilustrar esse pensamento. Como medir a conectividade entre instituições, entidades, empresas, grupos de pessoas e indivíduos em tempo real? É exatamente por isso que os relatórios de grandes consultorias são uma poderosa fonte de informação para você se posicionar no mercado.
Parceria visa ampliar cobertura 4G para impulsionar transformação digital no campo
Com uma rápida pesquisa é possível observar que existem diversos exemplos de como a combinação de Geoprocessamento e Inteligência Artificial está sendo aplicada na análise de dados espaciais. Uma delas é a utilização de imagens de satélite para monitorar a saúde das plantações e prever safras futuras. Cada empresa poderá se tornar uma provedora de serviços de análise com base nos seus próprios dados.
- O tratamento de dados para decisões automatizadas através de tecnologias conhecidas como “Machine Learning” utiliza e depende de um grande volume de “exemplos” ou modelos de treinamento para que a decisão seja a mais acertada possível.
- Ao aplicar esses princípios e medidas em seu trabalho, os profissionais de BI podem contribuir para um ambiente de análise de dados mais ético e responsável.
- Além dessas habilidades e conhecimentos técnicos, os profissionais de BI também precisam desenvolver habilidades interpessoais, como a capacidade de trabalhar em equipe e a capacidade de comunicar de forma eficaz.
- Se você ainda não sabe trabalhar com um dos principais provedores de Cloud Computing (AWS, Microsoft Azure e Google Cloud) comece imediatamente.
- Published in Bootcamp programação
Линкбилдинг Что Это? Методы Получения Ссылок 2024 Евробайт
Есть мнение, что форумы давно превратились в фермы ссылок с минимальным влиянием на продвижение в поисковиках. В 2023 году найти активные и модерируемые ресурсы тяжело, но в разных нишах и сейчас есть качественные площадки. Главный инструмент эффективного гостевого блогинга — качественные статьи.
Интерес к видео- и аудиоконтенту в последние годы значительно вырос. Если раньше можно было размещать подкасты на нескольких глобальных площадках, то теперь количество хостингов для подкастов значительно выросло. А это значит, что веб-мастер может получить десятки ссылок с минимальными усилиями. Каждый день в интернете появляется большое количество новостей, и не у всех есть время следить за ними.
- », как повторяют представители Яндекс при любом удобном случае, и выстраивание ссылочного профиля станет проще и намного эффективнее.
- Как правило, они предлагают различные пакеты, из которых они могут выбирать, в зависимости от их бюджета и потребностей.
- Линкбейтинг — это создание таких материалов, которые привлекают пользователей ссылаться на ресурс.
- В целом, веб-мастера могут повысить рейтинг своих сайтов, увеличив число высококачественных сайтов, которые ссылаются на их страницы.
- Тут наверное нужно было написать что-то в стиле «ссылки для людей; больше маркетинга чем search engine optimization; ссылки по которым кликают» и т.п.
Также крауд не есть норм, гугл активно борется с таким методом, большое количество таких ссылок быстро удаляются модераторами. Мне кажется, что вопрос не в том, какие ссылки работают лучше — а какие ставить оправданно.Ссылки, как и всё в маркетинге — это вопрос экономической целесообразности. Не буду оригинальным и скажу, что это dofollow-анкорные ссылки изнутри тематического контента с хороших доменов, в идеале — с трафиком по этим ссылкам. Но все, кто продвигают серые и чёрные тематики, знают, что часто достаточно обходиться tier-3 схемами и PBN без трафика по этим ссылкам.
Если они определят, что проект нарушает рекомендации по поисковой оптимизации, могут последовать ручные ограничения. Ссылочные факторы — ядро алгоритмов ранжирования в поисковых системах. линкбилдинг с чего начать На первых этапах развития Google именно ссылки были ключевым показателем качества ресурса. Если на него ссылались авторитетные сайты, алгоритмы понимали, что ему стоит доверять.
Для анализа ссылочной массы сайта существуют специальные инструменты веб-аналитики. Они позволяют не только отслеживать количество и качество внешних ссылок, но и вовремя обнаруживать угрозы санкций со стороны поисковых систем. Если инструменты аналитики фиксируют подозрительные, некачественные ссылки или резко возросшее число ссылающихся ресурсов, имеет смысл предпринять ответные действия. В частности, по возможности удалить спамные ссылки, которые могут негативно повлиять на восприятие сайта поисковыми алгоритмами.
Главный маркер неестественных бэклинков — отсутствие пересечения по тематике между донором и реципиентом. Google вкладывает много ресурсов в развитие алгоритмов определения искусственных ссылок и наказывает сайты, которые злоупотребляют этим. Хотя на практике ситуация со спонсируемыми ссылками не такая однозначная. Если не использовать много коммерческих анкоров с переспамом по ключам и добавлять в профиль естественные бэклинки, риск санкций от поисковых систем заметно снизится. Чтобы иметь возможность разместить ссылку с трастового сайта, необходимо обратиться к его администрации.
Площадка, на которой размещается статья со ссылкой, называется донором, а страница, на которую ведет линк, – акцептором. Суть публикации текста в том, что ресурс-донор предоставляет траст (доверие) странице-акцептору. Интересно, что траст напрямую зависим от того, сколько ссылок размещено. Чем их больше ведет на продвигаемый сайт, тем выше его позиции в рейтинге Google. Однако если вы можете добыть по настоящему качественные крауд-ссылки – сделайте это.
Авторитетность донора складывается из большого количества факторов. Необходимо обратить внимание на качество контента, объем трафика, положение в нише и другие особенности. Качество ссылки сильно зависит от того, на какой странице она размещена. Если на эту страницу сделана правильная перелинковка и есть бэклинки с авторитетных ресурсов, размещение можно считать эффективным.
С Авторитетного Веб-сайта
Как и любая маркетинговая стратегия, получение внешних ссылок имеет свои плюсы и минусы, которые стоит учитывать. Главная проблема с реализацией многоуровневого ссылочного профиля – это бюджеты. В качестве ссылок первого уровня используются ссылки, которые годятся для второго и даже третьего уровней, этим структура профиля и ограничивается. Такая структура менее эффективна, хуже контролируется и более уязвима во всех отношениях.

Бэклинки из социальных сетей — один из простых ответов на вопрос, как строить обратные ссылки. Особенность таких размещений в том, что они почти не влияют на рейтинг сайта в органической выдаче. Медиапроекты добавляют ссылки на источники, если используют при подготовке контента информацию из внешних ресурсов. Этим можно воспользоваться и распространить через сайты СМИ инфографику, исследование или другие инфопродукты. Для мониторинга использования изображений на внешних ресурсах можно применять IMATAG Monitor или сервисы с аналогичными возможностями. Если веб-мастер не соглашается добавить активную ссылку, есть основания для создания DMCA запроса на удаление контента в Google Images.
Текстовые Ссылки
Это группы ресурсов, создание и обслуживание которых выполняется исключительно для того, чтобы они служили источником линков. Но при этом ссылки из таких сайтов обеспечивают неплохой результат в некоторых типах ниш. Хотя за последние годы эффективность метода снизилась, а риски повысились, из-за чего от него все чаще отказываются. Тем, кто прибегает к линкбилдингу в качестве инструмента для внешней оптимизации, стоит также знать, что можно выбрать «срок жизни» ссылки. Цена при этом определяется самой площадкой, где планируется публикация.
Необходимо следить за тем, чтобы анкорные ссылки были равномерно разнесены по тексту, были записаны разными словами и вели на разные страницы. Особое внимание стоит уделить мониторингу бэклинков, потому что каждая потерянная ссылка — удар по репутации сайта. При наличии отрицательной динамики профиля рейтинг проекта в органической выдаче может снизиться. Ссылки из социальных сетей, сабмиты, размещения на отзовиках и другие условно-бесплатные методы частично скрывают SEO-ссылки и создают естественный ссылочный профиль. Спровоцировать естественный ссылочный взрыв можно с помощью вирусного контента и его распространения в социальных сетях, но такие кампании не всегда дают нужный эффект.
На этом ресурсе можно найти множество объявлений, где предлагают «качественные» ссылки. Их могут называть «белыми», контекстными, естественными и прочими привлекательными для внешней оптимизации терминами. Более того, даются разные гарантии, что линки легальные и помогут сайту в краткие сроки выйти в топ Google. Говоря о линкбилдинге, как про инструмент продвижения, стоит также отметить, что он помогает привлечь постоянный и релевантный трафик на сайт. Качественный, интересный и уникальный контент легко зайдет в топ сам по себе, без дополнительный «вливаний», если Яндекс поймёт, что пользователям он нравится. Парадокс в том, что на самом деле хорошие тексты легко получают естественную ссылочную массу.
Вы можете прочитать онлайн-обзоры, чтобы получить представление о том, что другие думают о качестве обслуживания. Было бы полезно, если бы вы приобретали ссылки только из тех сервисов, которые можете себе позволить. Списки каталогов https://deveducation.com/ — отличный способ представить ваш сайт новой аудитории. Размещая свой сайт в каталогах, вы можете повысить его видимость и привлечь новых посетителей. Нет никаких оснований ставить это под сомнение в ближайшие годы.

В завершение статьи рассмотрим основные типы и источники ссылочной массы, которые можно использовать в продвижении. PageRank — это показатель, используемый Google для измерения качества веб-сайтов. Сайты с более высоким PageRank с большей вероятностью будут занимать более высокие позиции в результатах поиска. Ссылки с качественных сайтов имеют больший вес, чем ссылки с некачественных сайтов. Использую, в основном, аутрич, крауд-маркетинг и контент-маркетинг. Потому как показатели авторитетности могут быть в порядке, но данные по трафику могут изменяться постепенно, если ресурс начал злоупотреблять продажей ссылок например.
Некоторые Популярные Методы Линкбилдинга
Поэтому можно создавать PDF и распространять их на релевантных площадках. Считается, что ссылки с площадок, где пользователи могут свободно обмениваться контентом, практически не влияют на рейтинг сайта в органической выдаче. Но они создают «подушку безопасности», которая снижает риск появления санкций.
Если использовать для распространения дайджестов площадки с целевой аудиторией, можно получить обратные ссылки из социальных сетей и других площадок. Поисковые системы считают ссылки из социальных сетей естественными, поэтому можно активно продвигать сайт на таких площадках и не переживать о санкциях. А если предложить аудитории качественный контент, получится даже создать активное сообщество в социальной сети. Сети персональных блогов обычно используют опытные SEO-специалисты, так как стратегия построения ссылок достаточно сложная и требует специфических знаний. Для создания PBN понадобятся определённое количество доменов, качественный контент и обратные ссылки. Q&A-сервисы вроде Reddit часто используются для линкбилдинга и входят в число самых доступных площадок для получения обратных ссылок.
Поэтому на помощь приходят дайджесты — подборки важных материалов с коротким пересказом и ссылкой на источник. Оптимизаторам проще купить несколько бэклинков на бирже, чем тратить время на составление технического задания, поиск автора и контроль распространения контента. В среде оптимизаторов давно обсуждается целесообразность использования ссылок на основе редиректов. Некоторые специалисты считают, что они не передают вес и нет ничего лучше стандартных бэклинков без любых атрибутов. Недостаток работы с PBN заключается в том, что на поддержку придётся тратить много времени.
PBN — сеть сайтов, созданных специально для ссылочного продвижения основного проекта. Ресурсы могут быть нейтральной тематики, например, новостными порталами, или быть посвященными теме главного проекта. Сеть сайтов можно создать самостоятельно, однако это потребует времени, сил и финансовых вливаний. Кроме того, PBN можно купить, но перед этим необходимо узнать не обслуживает ли она другие проекты. Те, которые отражают тематику контента и вписаны в текст гармонично, называются естественными.

Веб-мастера покупают ссылки и редко предлагают разместить упоминания в ответ, хотя такая тактика может принести пользу. При выборе методов построения ссылок стоит уделить особое внимание составлению анкор-листа. Желательно добавлять в него не только коммерческие ключи, но и фразы, которые будут выглядеть естественно в глазах алгоритмов.
Строить дом необходимо ориентируясь только на свои собственные желания и предпочтения, но затраты на это будут очень большими. Приобретать ссылки можно в такой бирже, как Sape, но ссылки там не всегда лучшего качества. Такие ссылки являются менее естественными, но могут приносить трафик, если статьи размещены с качественных ресурсов. Такие площадки релевантны вашей тематике, поэтому найти их не сложно. Outreach — это ручной поиск информационных партнеров, которые заинтересованы в размещении вашего материала (статьи, новости) на своем портале. Обращаясь к будущим партнерам, предложите им качественный и оригинальный контент, например бесплатный гостевой пост, и взаимную рекомендацию их веб-ресурса.
- Published in IT Образование
What will be the worlds future reserve currency?
This protocol would effectively reduce the influence of any one country and ostensibly would force more prudent economic policies. Known as the Bretton Woods Agreement, it established the authority of central banks, which would maintain fixed exchange rates between currencies and the dollar. In turn, the United States would redeem U.S. dollars for gold on demand. Countries had some degree of control over currencies in situations where the values of their currencies became too weak or too strong relative to the dollar.
It is the most commonly held reserve currency and the most widely used currency for international trade and other transactions around the world. The centrality of the dollar to the global economy confers some benefits to the United States, including borrowing money abroad more easily and extending the reach of U.S. financial sanctions. In the beginning, the world benefited from a strong and stable dollar, and the United States prospered from the favorable exchange rate on its currency. The foreign governments did not fully realize that although gold reserves backed their currency reserves, the United States could continue to print dollars that were backed by its debt held as U.S. As the United States printed more money to finance its spending, the gold backing behind the dollars diminished.
Japanese yen
One measure of confidence in a currency as a store of value is its usage in official foreign exchange reserves. As shown in Figure 2, the dollar comprised 60 percent of globally disclosed official foreign reserves in 2021. This share has declined from 71 percent of reserves in 2000, but still far surpassed all other currencies including the euro (21 percent), Japanese yen (6 percent), British pound (5 percent), and the Chinese renminbi (2 percent). Moreover, the decline in the U.S. dollar share has been taken up by a wide range of other currencies, rather than by a single other currency. Thus, while countries have diversified their reserve holdings somewhat over the past two decades, the dollar remains by far the dominant reserve currency. The currency most commonly held as a foreign exchange reserve is the U.S. dollar, which, according to the International Monetary Fund (IMF), comprised nearly 62% of allocated reserves as of late 2012.
A reserve currency is a foreign currency that a central bank or treasury holds as part of its country’s formal foreign exchange reserves. Countries hold reserves for a number of reasons, including to weather economic shocks, pay for avatrade review imports, service debts, and moderate the value of their own currencies. In 1944, during World War II, 44 nations met and decided to link their currencies to the U.S. dollar, the U.S. being the strongest power among the Allies.
Critically, the reallocation came through changes in new investment flows, not by selling the stock of existing positions. Why are countries moving away of their dependence on the US Dollar as their world Reserve CurrencyThe US Dollar has been the world’s reserve currency since 1945. The US Dollar is by far the most frequently used currency in international commerce, and it is also the most liquid.
The reserve currency can be used in international transactions, international investments and all aspects of the global economy. As a result, the depth and liquidity of U.S. financial markets is unmatched, and there is a large supply of extremely safe dollar-denominated assets. That said, this dominance should not be taken for granted and the note ends with a discussion of possible challenges to the dollar’s status.
Top financial concerns in a divorce and how to plan for them
Typically, but not always, a reserve currency is free floating and easily convertible, issued by an independent central bank and widely used in global business transactions. Delegates from 44 Allied countries met in Bretton Wood, New Hampshire, in 1944 to develop a system to manage foreign exchange that would not disadvantage any country. The delegation decided that the world’s currencies would no longer be linked to gold but pegged to the U.S. dollar. Other countries may employ fixed exchange rate schemes for a variety of reasons. Under this type of system, supply and demand can move the value of its national currency higher or lower. For instance, increased demand due to a relatively strong economy would lead to a higher value for a country’s currency.
- It came down to two different plans put forward by two very different men.
- The run on gold was so extensive that President Nixon was compelled to step in and decouple the dollar from the gold standard, which gave way to the floating exchange rates that are in use today.
- Manipulating and adjusting the reserve levels can enable a central bank to prevent volatile fluctuations in currency by affecting the exchange rate and increasing the demand for and value of the country’s currency.
- But some experts argue that high foreign demand for dollars comes at a cost to export-heavy U.S. states, resulting in trade deficits and lost jobs.
According to the International Monetary Fund (IMF), the USD accounts for 59.15% of the total allocated global reserve currency, with the euro the second most widely held at 20.48%. The status of a reserve currency means that the particular currency is held in large amounts as part of a coordinated foreign currency reserve program. De-dollarization is the shrinking of the influence that the U.S. dollar has on the economies of other countries. Even as countries aim to reduce dependency, the dollar was the most widely held reserve currency in 2022. A world currency is any money that can freely be used or exchanged for another currency inside or outside the borders of the country that issues it. The first U.S. dollar (USD) is the official currency of the United States and several other countries.
Understanding Currency Reserves
As a result of the Bretton Woods Agreement, the U.S dollar was officially crowned the world’s reserve currency, backed by the world’s largest gold reserves. Instead of keeping supplies of gold, other countries accumulated reserves of U.S. dollars; central banks would maintain fixed exchange rates between their currencies and the greenback. After the war ended, the restructured governments of the former Axis powers also agreed to use dollars for their currency reserves. A key function of a currency is as a store of value which can be saved and retrieved in the future without a significant loss of purchasing power.
The U.S. economy surpassed that of the United Kingdom, though world commerce still centered around the U.K., with transactions taking place in British pounds. These reserves are rounded up to the nearest billion; they include gold, U.S. dollars, and other reserve currencies. A highly valued dollar makes U.S. imports cheaper and exports more expensive, which can hurt domestic industries that sell their goods abroad and lead to job losses. This imbalance can worsen during times of financial turmoil, when investors seek the stability inherent to the dollar. Some analysts argue that the cost of the dollar’s dominance for manufacturing-heavy U.S. regions such as the Rust Belt are too high, and that the United States should voluntarily abdicate. Other economists disagree, arguing that there will always be winners and losers with a strong dollar.
As a result, foreign nations closely monitor the monetary policy of the United States to ensure that the value of their reserves is not adversely affected by inflation or rising prices. Saudi Arabia also holds considerable foreign exchange reserves, as the country relies mainly on the export of its vast oil reserves. If fxpcm oil prices begin to rapidly drop, the country’s economy could suffer. It keeps large amounts of foreign funds in reserves to act as a cushion should this happen, even if it’s only a temporary fix. Some commentators posit a more radical shift in currency positioning, where dollar reserves are dumped on the open market.
For nearly a century, the United States dollar has served as the world’s premier reserve currency, taking the crown once worn by the pound sterling. The future of the dollar as the most popular reserve currency is less certain. When a country acquires reserves, it doesn’t place the currency in general circulation.
The number of currencies that are in use today has grown significantly from the 70s. This is due to the fact that many nations have adopted their own currencies in their nation’s financial system. So representatives prtrend from 44 nations gathered in the small town of Bretton Woods, New Hampshire to come up with the solution. For Foreign Affairs, Peking University’s Michael Pettis looks at the high price of dollar dominance.
The latest addition, introduced in October 2016, is China’s yuan or renminbi. Increased European integration is one possible source of challenge, as the European Union (EU) is a large economy with fairly deep financial markets, generally free trade, and robust and stable institions. During the COVID-19 crisis, the EU made plans to issue an unprecedented amount of jointly backed debt. If fiscal integration progresses and a large, liquid market for EU bonds develops, the euro could become more attractive as a reserve currency. This integration could potentially be accelerated by enhancements to the EU’s sovereign debt market infrastructure and introducing a digital euro.
The increase monetary supply of dollars went beyond the backing of gold reserves, which reduced the value of the currency reserves held by foreign countries. Russia’s foreign exchange reserves are held mostly in U.S. dollars, much like the rest of the world, but the country also keeps some of its reserves in gold. Since gold is a commodity with an underlying value, the risk in relying on gold in the event of a Russian economic decline is that the value of gold will not be significant enough to support the country’s needs. As of February 2022, Russia’s foreign exchange reserves totaled some $630 billion.
It’s hard to see how tanking the economy of their biggest customer would benefit them. The resulting global turmoil would almost certainly destabilize their own economies more than the U.S. dollar and create a self-inflicted domestic political crisis. Countries like Japan and China—which have the largest trade surpluses—also have the most currency reserves because they receive U.S. dollars and other foreign currencies when they provide exports.
- Published in Forex Trading
Seven Common Fears in Recovery and Why Sobriety Is Still Worth It Promises Behavioral Health
Eventually, other people will know you have a problem. Rather than waiting for them to find out after a terrible accident or losing your job, seek help now. You can choose how much to tell them about where you’re going and why.
- You may be afraid to stop using because you have no idea what life will be like after you do.
- Many times, social events and outings center around drinking alcohol.
- More recently, he went to a clinic for infusions of ketamine, and tried tiny doses of psychoactive mushrooms.
- These are thoughts that run through every addict’s mind.
You recognize what you’ve put them through, you’re ashamed of it and you wish you could take it back. Yet, at the same time, it may feel better just to give in and use because that’s what they expect from you. If you try to stop using and fail, you’re disappointing them all over fear of being sober again. Look what I’ve done to my life.” This is a very common thought process. After detox, your brain begins to piece together the problems you now have with relationships, work, school or other important aspects of your life. It’s disheartening to realize what you’ve lost.
Fear of Being Sober: How the NA Steps Help You Say Goodbye to a Life of Drugs
You probably feel ashamed about your struggles with addiction. One of your fears in recovery may also relate to thoughts about being judged when you enter a residential treatment facility. This is especially true if you’ve been able to hide your addiction up until now. How will you explain your absence to everyone? You might even think that addiction rehab is all about shaming addicts with their addiction and trying to force them to quit.
- You’ll find your way, and you’ll be even more you without substances controlling your mind.
- Whether you have one day sober or 10 years, recovery presents challenges.
- What you once thought of as fun will pale in comparison to a life rich in reality, one that is completely drug and alcohol-free.
- Choosing sobriety and sticking with it gives you the confidence to pursue anything.
Find a facility that emphasizes developing individualized plans that meet your particular needs rather than a one-size-fits-all treatment program. And don’t worry, your tastes and style are not actually tied to drugs. You’ll find your way, and you’ll be even more you without substances controlling your mind. Getting sober also means you have to admit that you have a substance abuse problem, which for many people is scary enough in itself. Unfortunately, it is these fears (and more) that often stop addicts from getting the help and treatment that they need to stop using.
Sober Hour
In some cases, it’s more complicated than that. Maybe these people have been in your life since childhood, and you’ve all fallen into the same trap. You’ve got history, but you’ve also got baggage. If a booked social calendar is important to you, you’ll find ways to be proactive and realign what you do to fit your new lifestyle. The truth is, you have no idea what success will look or feel like.
- Sobriety means having to face uncomfortable truths about ourselves and others and having to stand up and be who we are.
- The fear of getting sober is more common than we may think.
- People you love will die, you will move, you may experience the end of a relationship, and you may even lose your job.
You’re not obligated to drink just to make others feel good about their drinking. So don’t allow anyone to make you feel that way. This is the hard part, but it’s also the most rewarding.
Define Your Fear to Overcome It
But when you are in treatment, you learn how to deal with stress so that it does not build up and immobilize you. New coping skills and behavior modifications will enable you to tackle whatever life throws your way. Additionally, you will always have the support of your group and allies to help talk you through any crises that arise. If you commit to it, there is hope for coping with life’s stresses without drinking. After months or years of being fixated on drugs and alcohol, who are you if you arent an addict? These are some of the most difficult questions in recovery, and the answers may change over time.
- Published in Sober living





